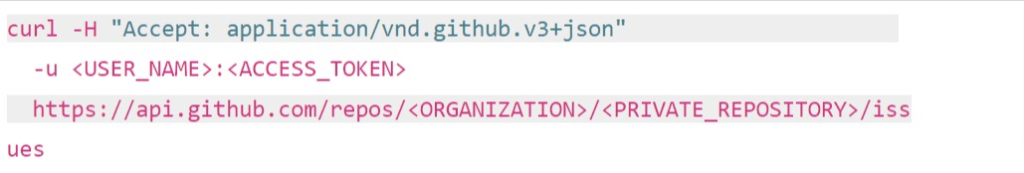
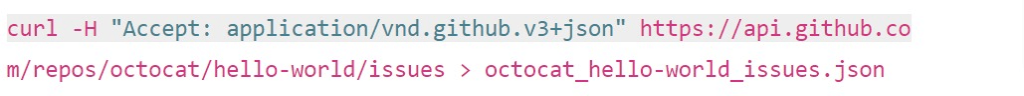
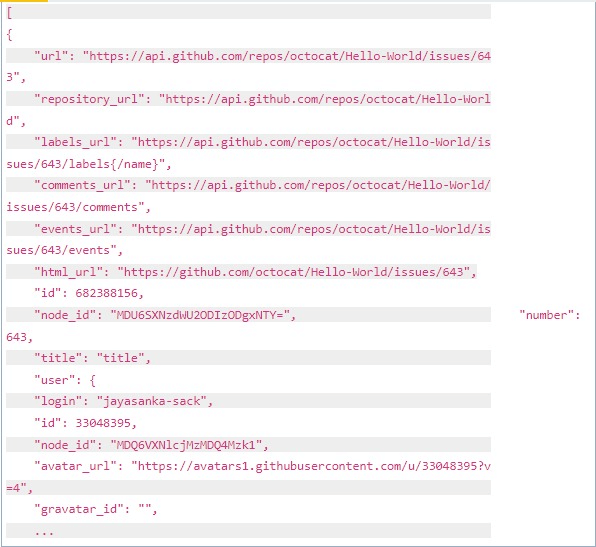
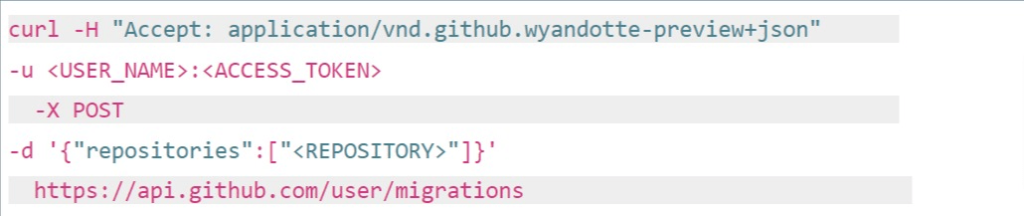
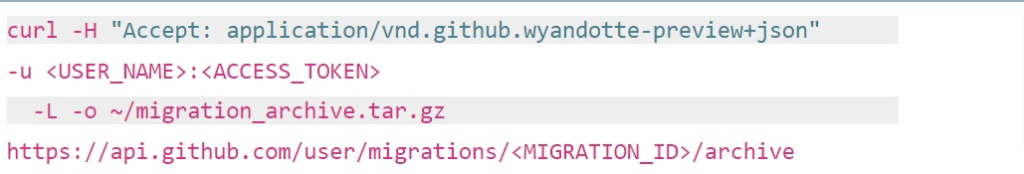
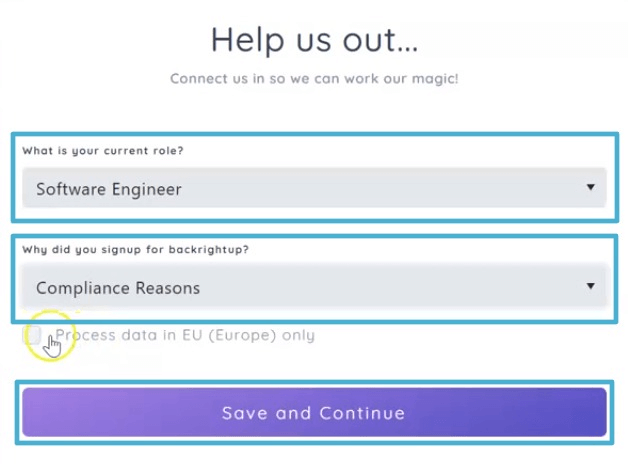
Since originating from the collaboration with the US Department of Defense through Microsoft, Backrightup has evolved to secure Azure DevOps and GitHub environments globally, serving the most compliance-driven sectors, including financial services, government, engineering, and healthcare. This DNA underscores its capability to safeguard the most sensitive and critical data against a broad spectrum of DevOps risks, ranging from inadvertent deletions to sophisticated cyber threats. Trusted by the world’s largest organizations, Backrightup stands as a testament to Microsoft for unmatched security and resilience, ensuring that Azure DevOps data remains protected under all circumstances.
Comprehensive Coverage for Work Items and Boards
Backrightup’s unlimited backup for Work Items and Boards ensures that every attachment and interlinked item is meticulously preserved. This level of detailed backup maintains the integrity of complex project workflows, guaranteeing full recovery capability with top-tier encryption for utmost security.
Unmatched Git/TFVC Repository Backup
Acknowledging the critical value of source code, Backrightup delivers robust backup solutions for Git and TFVC repositories. It secures every line of code with unique encryption keys, offering developers the assurance that they can securely revert to any version at any time.
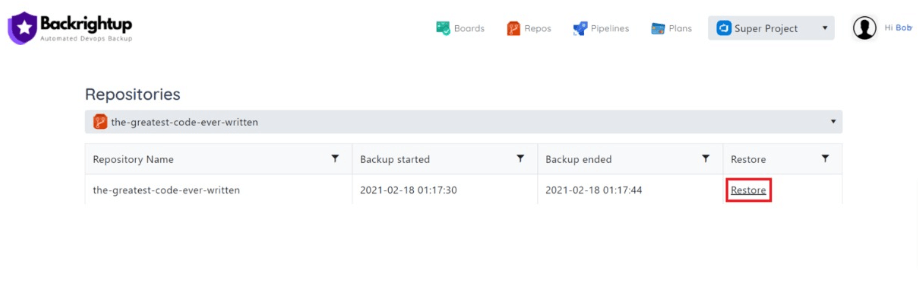
On-Demand Backup Usage
Integration with existing pipelines for unlimited on-demand backup capabilities demonstrates Backrightup’s flexibility. This allows teams to implement backups at any developmental stage, providing immediate data protection and peace of mind.
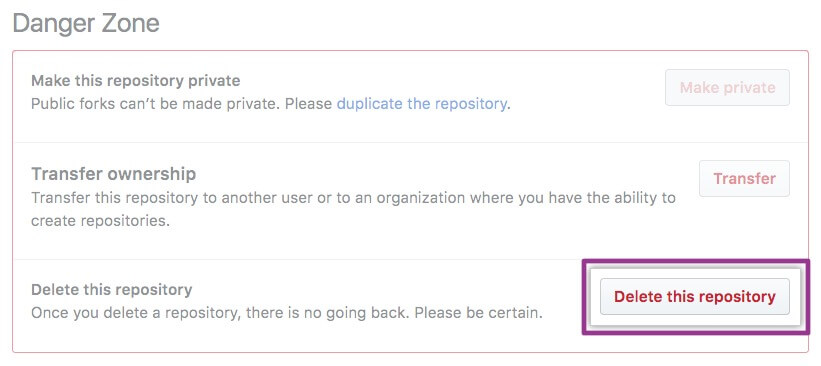
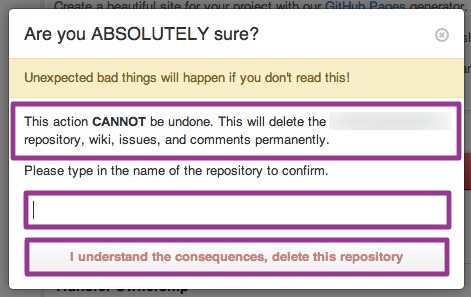
Full Spectrum Backup and Restore
Backrightup extends its protection to every component of Azure DevOps, from Pipelines and Releases to Wikis. This comprehensive approach ensures that the entire DevOps ecosystem is covered, leaving no aspect of your operations vulnerable.
Round-the-Clock Technical Support
Global technical support and restore assistance ensure that help is readily available, minimizing potential downtime and keeping business operations running smoothly.
Data Sovereignty and Flexible Retention
Backrightup’s flexible data retention policies and compliance with data sovereignty laws offer customizable solutions to meet a variety of organizational needs, aligning with legal and regulatory standards. As an example, Backrightup work with Financial Service organizations in the US, Canada, EU, Australia and New Zealand.
Continuous Innovation
A commitment to continuous improvement ensures that Backrightup remains at the industry forefront, with regular feature updates and product strategy reviews to meet evolving customer needs. Backrightup understand that every organization is different so work with customers to customization so the solution is integrated into their data governance and compliance requirements.
Dedicated Account Support
Dedicated training and support are provided to maximize the potential of Backrightup, ensuring a smooth onboarding process and optimized data protection strategies.
Proactive Reporting and Notifications
Comprehensive reporting and real-time notifications offer robust data monitoring and governance, keeping organizations management informed about the health and security of their data.
Tier 1 Security for Regulated Organizations
Backrightup meets the highest security standards required by regulated organizations, providing custom contracts, security assessments, and onboarding to ensure compliance and data protection.
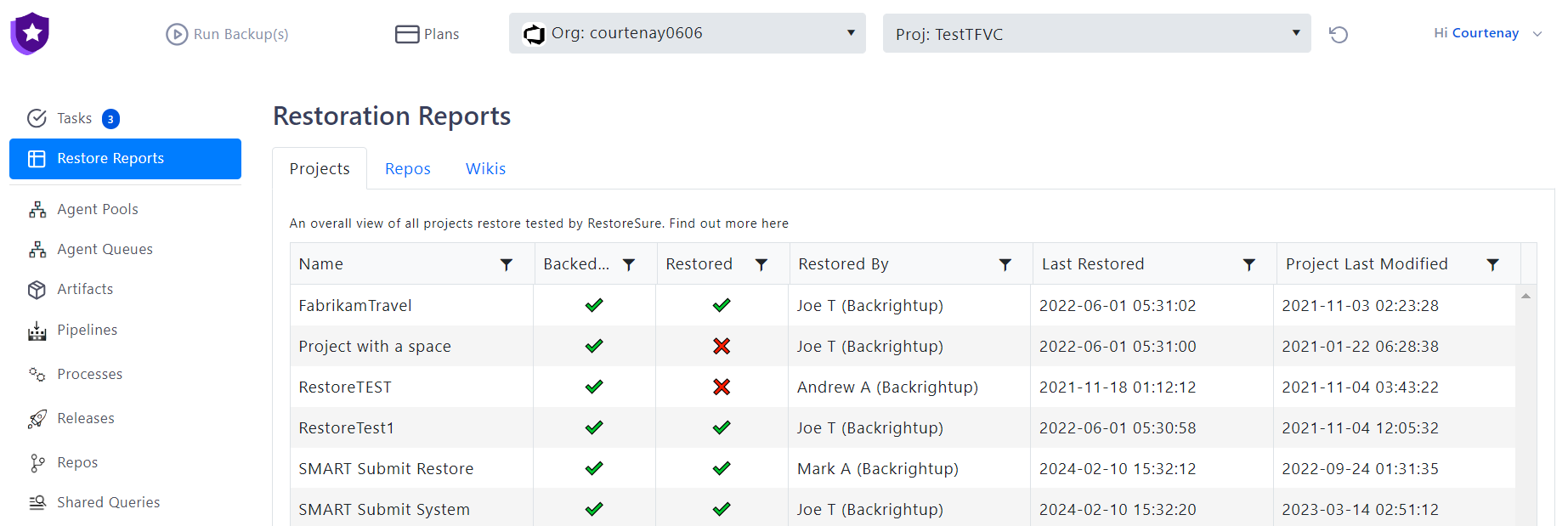
Dedicated Restore Testing
Backrightup guarantee efficacy and work with their customers on restore testing and full reporting services, offering an additional layer of assurance during a disaster in the reliability of the backup and restore processes.
Conclusion
Backrightup is not merely a backup tool; it’s a comprehensive solution that underpins the data protection strategy, developed from high-stakes origins and trusted by leading organizations across the most regulated industries worldwide. Its coverage, flexible backup options, and dedicated support make it the definitive choice for securing Azure DevOps environments against any threat. With Backrightup, organizations ensure the continuity, integrity, and security of their most valuable digital assets, addressing compliance demands, and solidifying its status as the preferred Azure DevOps data protection solution.
For more information, get in touch to speak with one of our Azure DevOps Experts.