This guide provides a straightforward overview of GitHub storage limits and outlines effective ways to manage them.
GitHub offers a decent amount of storage for your Git repositories.
However, GitHub sets file and repository size limits to make repositories easier to maintain and work with while keeping the platform running smoothly.
GitHub’s storage limitations can be challenging when working with data and files of large sizes.
The good news is that there are tips and tricks to help you overcome GitHub’s storage limits—starting with the best practices and recommended tools below.
Table of Contents
3 Practical tips for working around GitHub storage limits
- Create smaller files
- Use Git Large File Storage
- Avoid pushing your file to GitHub
Tools to handle GitHub storage limits
- Backrightup
- Git LFS
- BFG Repo Cleaner
Frequently asked questions
- How do I know the amount of storage I use on GitHub?
- How can I upload files larger than 100 MB to GitHub?
- What are GitHub’s size limits?
Resources you will love
Overcome GitHub storage limitations
3 Practical tips for working around GitHub storage limits
Keep in mind the best practices below to handle limitations on GitHub storage and simplify managing large files.
1. Create smaller files
Create smaller files from your big ones in GitHub to avoid taking up all the allowed storage limits.
While this might not always be ideal, it can help you reduce your stored file sizes in GitHub.
For example, if you use Python, import your data separately from your computing platform and save it as a specific data structure.
Then, break down the data into smaller structures, export the smaller files separately, and delete the large file that takes up most of your GitHub storage.
It can be a tedious solution so use it sparingly and only when necessary since it can take a lot of work.
Creating smaller files also forces you to break down and separate data into groups when it should be a single file. It can lead to potential issues and adds more file clutter to your GitHub repositories.
2. Use Git Large File Storage
One of the best ways to preserve your commit history and the project’s integrity is to use Git Large File Storage (LFS).
Git LFS deals with large files by storing the files’ references in the repository but not the actual file.
It creates a pointer file that acts as an actual file reference stored somewhere else (LFS server), working around Git’s architecture.
GitHub can manage the pointer file within your repository.
Plus, GitHub uses the pointer file as a map to your large file when you clone the repository down.
Essentially, Git LFS intercepts the designated files when you commit and push in GitHub and migrates them to the LFS server.
Once you install Git LFS on your local device, you can use three lines of code to install LFS in your repository and track the CSV files within.
Git LFS also lets you look and view the files that are being tracked using a command line.
After committing the file to your repository, use git-lfs-migrate to add it to the LFS and remove it from your Git history.
The process can help you save on storage since you’re not storing the actual files within GitHub.
However, LFS has a ceiling you can only exceed by paying the required fee.
Discern and use common sense to determine whether using Git LFS (and potentially paying more) is the best option for you.
3. Avoid pushing your file to GitHub
Another way to help you work around GitHub’s storage limits is to add the filename in your repository’s .gitignore file instead of sending the actual file to GitHub.
This way, you can keep a local copy of your data and provide a URL to the data source in your project’s README.
It’s not always a great option if you gathered and created your dataset, but it can be a good solution for data that’s already packaged on the web.
You can create a .gitignore file in your repository’s parent directory and store the file directories you want Git to ignore.
Use a wildcard symbol (*) so you won’t need to manually add individual files and directories every time you make a new large file.
Git will automatically ignore them so they won’t get uploaded to GitHub, saving storage space and preventing common error messages.
Tools to handle GitHub storage limits
The following tools can help you manage your GitHub files and deal with the platform’s storage limits better.
Backrightup
One of the ways to save storage space is to back up your GitHub repositories.
This way, you can keep backups of your files and store them in other locations, freeing up space.
Running regular backups also helps keep you from losing data in case of malicious software attacks, accidental deletions, server crashes, errors, and other issues.
However, you want to simplify your GitHub backup process to lighten your workload and keep your workflows moving seamlessly.
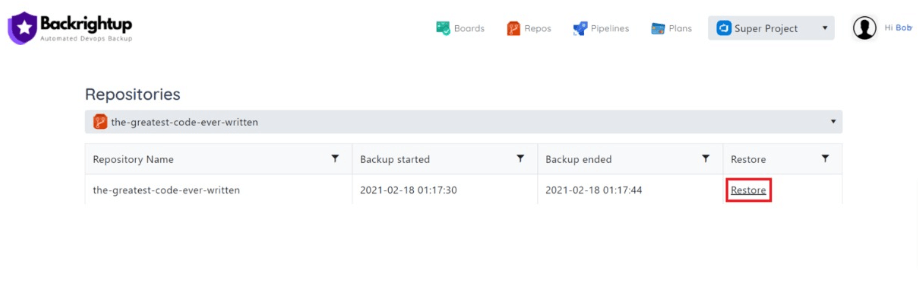
An excellent solution is to use Backrightup, our automated backup platform and service for Azure DevOps, Gitlab, Bitbucket, and GitHub.
Our backup service automates your GitHub backup and restores, making recovering your repository and data quick and easy.
Our solution also provides full backup storage to your preferred locations, and you won’t need to maintain your backup scripts.
Git LFS
Git LFS can track the files beyond GitHub’s storage size limit.
As mentioned, Git LFS makes pointer files that reference the actual files usually stored in the LFS server.
Git LFS lets you store files up to the following:
- 2 GB for GitHub free
- 2 GB for GitHub Pro
- 4 GB for GitHub Team
- 5 GB for GitHub Enterprise Cloud
Git LFS silently rejects new files you add to the repository if you exceed the 5GB limit.
BFG Repo Cleaner
The BFG is an alternative to git-filter-branch that allow for easier and faster cleansing of bad data from your Git repository history, freeing up GitHub storage space.
The BFG Repo Cleaner can help you clean up massive files and remove credentials, passwords, and other confidential data stored in GitHub.
You can even use Scala language when necessary to customize the BFG.
Frequently asked questions
Below are the common questions people ask about GitHub storage limits.
1. How do I know the amount of storage I use on GitHub?
You can view your GitHub Packages usage for your personal account in the Access section of the GitHub sidebar.
Click Billing and plans. You can see your usage for data transfer details under GitHub Packages.
To see your storage usage for GitHub Packages and GitHub Actions, go to Storage for Actions and Packages.
2. How can I upload files larger than 100 MB to GitHub?
GitHub places hard limits on file and repository sizes.
It has a 100MB file limit, so you’ll need to use Git LFS.
You can place git-lfs into your $PATH to download and install it.
3. What are GitHub’s size limits?
GitHub limits the maximum file size (or sizes) you can add to your repository to 50 MB.
File sizes larger than 50 MB will get you a warning from Git.
It is strongly recommended to keep your repositories small, ideally less than one to five GB, to minimize performance impact on GitHub.
Resources you will love
- How to Organize GitHub Repositories
- Top GitHub Backup Tools
- GitHub Backup Ultimate Guide: Tips, Steps, Tools
- Top 10 GitHub Security Best Practices
Overcome GitHub storage limitations
GitHub’s storage limits might not always be ideal for you and your work, but there are strategic ways to work around these limitations.
You can create smaller files and use reliable tools such as Backrightup to back up your GitHub repositories easily and save storage space.
Try Backrightup now to experience our GitHub backup solution’s benefits.