
If hackers were to attack your Azure DevOps repos now, are you confident they won’t succeed at infiltrating and decrypting or stealing your business-critical code and data?
As you’ll see below there are a plethora of threats that could affect your Azure Devops data Do you have Azure DevOps backups to ensure your data is secure and help you continue operating when that happens?
When operating on your Azure DevOps repositories, you can’t afford to be lazy about securing them because the tactics of cybercriminals are evolving fast.
One essential way to combat these threats is to have a firm grasp of the modern security threats surrounding your Azure DevOps repos and the elementary defenses you can establish.
What are Azure DevOps repos?
Azure DevOps repos are the modern day source control system. Whilst previously companies used tools like Team Foundation Server, Azure Devops repos bring this functionality to the cloud, allowing you to control your content versions, organize your project code and control the deployment of this code to various downstream environments.
It also helps you coordinate with your team regarding code updates and lets you track your solutions, code, builds, pushes, pull requests, commits, and branching project information.
Modern security threats to Azure DevOps repos
Below are some of today’s sophisticated security threats that put your Azure DevOps repository at serious risk:
Ransomware
Ransomware is still one of the most prevalent and destructive cybersecurity attacks against corporations and other vulnerable industries worldwide.
According to the US Department of Justice, since January 2016, more than 4,000 ransomware onslaughts occurred every day, soaring by 300% from approximately 1,000 daily hits in 2015. One report also revealed there were 61 million ransomware detections in 2019.
Ransom demands also skyrocketed. In 2019 alone, average payments rose by 104% from nearly $41,200 to almost $84,120. In 2020, some demands even reached over $40 million.
These ransomware attacks take a toll on industries because of their hefty fees and the hackers’ advanced extortion and data theft tactics and targets.
From individual computers and networks, hackers now assault BitBucket and GitHub code repositories by encrypting them.
A GitHub search shows that more than 392 GitHub repositories so far received ransom demands.
The hackers’ new scheme involves breaking into their accounts and exploiting the file processing code to render the stored data inaccessible.
This is devastating since codes posted in these private developer repositories are valuable and serve as intellectual property. Account-holders are bound to pay to retrieve them.
If the encrypted code affects large-scale projects or is the foundation for a company’s products and services (typically SaaS), businesses can lose massive heaps of money — or shut down.
Reports reveal that one of these hacked repositories charged a decryption fee of 0.1 Bitcoin (equivalent to $590) sent to their Bitcoin address.
Account hijacking
A series of bugs linked together can give cybercriminals smooth access to private Microsoft accounts if they can trick unknowing users into clicking malicious links.
A bug hunter in 2018 found that he can link an unconfigured Microsoft subdomain to his Azure instance and manipulate any piece of data received.
The Microsoft Sway and Store apps can also be fooled into deploying authentical login tokens to controlled unconfigured domains once users enter through Microsoft’s Live login system.
This means hackers can hijack any Microsoft Office account, which includes Azure DevOps, business accounts, and the data, emails, and files therein.
This scenario can happen to developer repositories too. In 2019, A Canonical-owned account on Github had its login credentials breached and used to create issues and others.
Internal malicious players
Security threats are not only external but can also be inside jobs.
In 2021, a previous IT consultant purposefully erased more than 1,200 Microsoft Office accounts of the company he retaliated against for his two-year jail time.
The result was a two-day total operational shutdown for the business, with costs as high as $560,000, and issue remediations for three months.
How to guard your Azure DevOps repos from security threats
Whether the threat is external or internal, fortifying your Azure DevOps repositories is an absolute must for your company. Here are two ways to protect your Azure DevOps repos:
Backup your Azure DevOps repos regularly
Protect your Azure DevOps repository by constantly backing them up. One way to make secure copies of that rich content is through third-party software tools such as Backrightup.
Backrightup is an automated tool for one-click Azure DevOps backups, especially those with business-critical code and content.
Upon linking Backrightup with Azure DevOps, it automatically extracts and creates copies of everything in your Azure DevOps Repos, including wikis, Work Items, Pipelines, Releases, and more — every day.
That means you don’t need to do this burdensome, time-consuming task yourself.
On the Backrightup dashboard, you’ll find the projects the tool copied from your Azure DevOps:
You’ll even see updates on Backrightup’s activities of duplicating which items and when.
Depending on the project or repository, the tool shows you relevant details such as last updated, backup started/ended, ID number, version, etc.
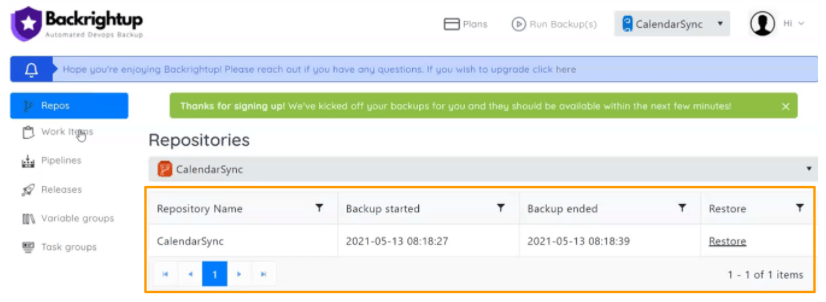
Plus, with a single click of the Restore button or link, you can retrieve selected items from the updates table.
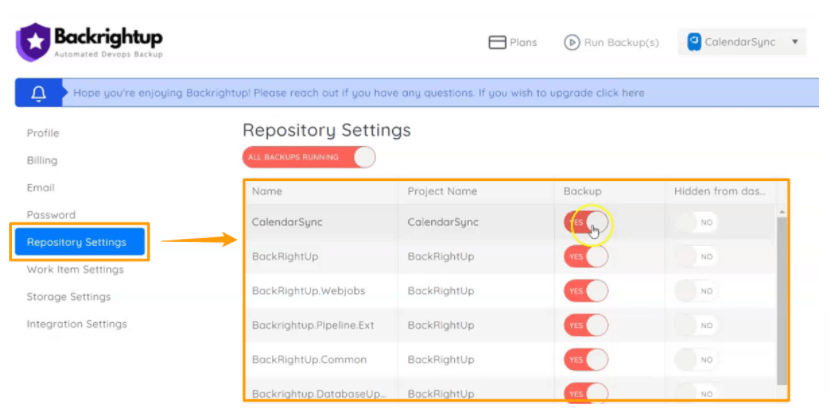
If you wish Backrightup instantly copied some and not all of your files, you can adjust the choices on Repository Settings.
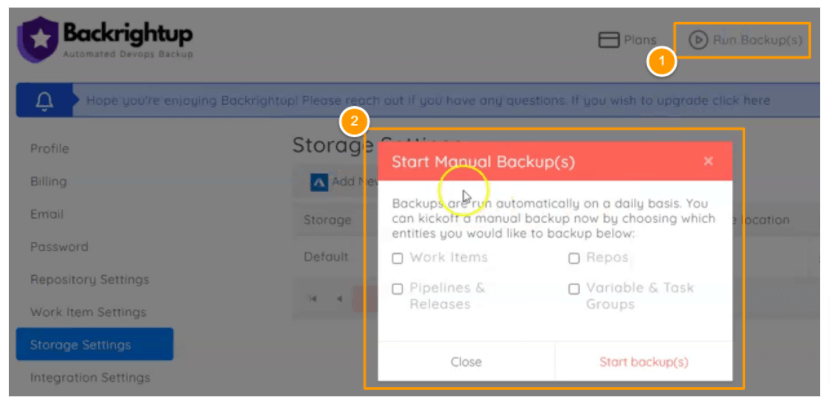
Or, if you can’t wait for the next day’s automatic updates and want Backrightup to duplicate specific items right now, do so by clicking Run Backups at the top of the dashboard:
With Backrightup, you get personalized, safe code backups in a few minutes, even without maintaining backup scripts.
What’s more, you don’t need to fear suddenly losing your backups or experiencing constant Azure DevOps API updates that can alter your codes, items, organizations, etc.
Bolster your cybersecurity policies and programs.
Fortify your company’s cybersecurity to protect your Azure DevOps repos against cybercriminals.
Establish rigid policies and procedures about information security, e.g., stating the authorization level required to access your codes, and others.
Include disciplinary measures and remedies should your staff and executives violate these security policies.
Next, implement risk management planning and adoption of robust cybersecurity tools and frameworks. This should include sufficient training for employees and executives on all levels.
Finally, set up and maintain all your security mechanisms and architecture — whether on the Internet, internal IT landscape, physical infrastructure, cloud, company and employee-used devices, and others — including, most importantly, your source control management system.
Additional steps to secure your Azure DevOps repositories and data
Actively engaging in your protection measures can help secure your Azure DevOps data and repositories.
After all, your project data and repositories are only as protected as the end-user access points.
Take essential and additional measures to cover all your bases and secure everything, including the following tips.
Set up two-factor authentication
If unauthorized users and malicious actors can’t access your organization, they won’t likely get to your data and repositories.
One way of ensuring only users with the right credentials can access your organization is to restrict access with two-factor authentication (2FA).
Azure Active Directory (AD) allows you to set up 2FA via phone authentication on top of a username and password for authentication requests.
Implement data classification
Classifying your Azure DevOps data makes tracking, tracing, and seeing changes or issues easier in case of an attack or data loss.
You can classify your data according to risk horizon, sensitivity, and the potential damage that may occur when the data gets compromised.
You can also adopt existing classification methods from your internal company or enterprise data to your Azure DevOps projects and repositories.
Use reliable encryption tools
Increase your sensitive projects’ protection using a robust encryption tool.
For example, you could use a tool that encrypts your computer’s entire drive and the stored data.
Some tools can automatically encrypt new files you save or store in the same drive.
Encryption like this can help prevent unauthorized access to your project data’s copies in case your desktop or laptop falls into the wrong hands.
Ensure secure access to your Azure DevOps organization
Azure AD allows administrators to control access to Azure apps and resources, including Azure DevOps.
Azure AD assesses your pre-set user access conditions to an app. Users are then authenticated when the access requirements are met.
Other conditional access policies and custom authentication mechanisms you can employ on Azure DevOps include the following:
- OAuth
- Personal access tokens
- SSH keys
- Alternate authentication
However, if users access Azure DevOps via a third-party client, only IP-based policies, specifically IPv4 based, are honored.
You can also use Azure AD to manage your organization’s access with user credentials more securely.
The feature lets IT departments manage the following:
- Password complexity, refreshes, and expiration for users who left your organization
- End-user access policies
You can also link Azure AD to your organization’s main directory via the AD federation. It allows you to manage all your Azure DevOps and Enterprise projects, data details, and access from one place.
Limit using alternate authentication credentials
Git-related tooling has alternate authentication as its default.
The mechanism lets end users configure alternate usernames and passwords during Git command-line operations.
You can also use the same username and password to access other data where you have permission.
However, while alternate authentication credentials are sent over HTTPS and password complexity requirements apply, these are often less secure than default federated authentication.
You can increase security even when using alternate authentication for your Azure DevOps organization.
For example, you could assess whether your organization needs additional policies to meet your project and repository security needs.
If not, you could disable alternate authentication credentials and choose a more secure authentication methods that address your requirements.
Safeguard your Azure DevOps repositories now
Backing up and protecting your Azure DevOps now — not later — should be one of your company’s top priorities.
After all, if your Azure DevOps data is compromised through criminal activities, Azure DevOps API updates, etc., your company could easily incur thousands of dollars worth of cost on repairs and to get everything up and running.
Azure DevOps backups and security are worth every bit of your time and investment. If you’re eager to kickstart your backups, contact us through our chat widget or email us now at [email protected].
